Smart machines and applications are steadily becoming a daily phenomenon, helping us make faster, more accurate decisions. The role of AI and machine learning is set to increase dramatically over the next five years, with more than 75 percent of businesses investing in Big Data. Organizations are spending almost 15 percent of their IT budget on machine learning capabilities. Let …
Read More »INSIGHTS
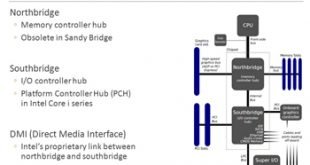
Intel I/O Controller Hub – Part 4
A family of Intel southbridge microchips, I/O Controller Hub (ICH) is used to manage data communications between a CPU and a motherboard. This specifically holds for Intel chipsets based on the Intel Hub Architecture. It is designed to be paired with a second support chip known as a northbridge. The ICH is used to connect and control peripheral devices. ICH8 …
Read More »Intel I/O Controller Hub – Part 3
A family of Intel southbridge microchips, I/O Controller Hub (ICH) is used to manage data communications between a CPU and a motherboard. This specifically holds for Intel chipsets based on the Intel Hub Architecture. It is designed to be paired with a second support chip known as a northbridge. The ICH is used to connect and control peripheral devices. ICH5 …
Read More »5 Cyber Security Myths for Linux Users
When Linux was born in 1991, it was an oddity in a changing world. Over the next decade, it rapidly elicited interest from the technology and developers communities globally, mostly for its open and democratic nature. By 2008, it had an almost USD 25 billion ecosystem. Today, many commercial, non-profit and even government organizations across the world prefer to use …
Read More »Intel I/O Controller Hub – Part 2
A family of Intel southbridge microchips, I/O Controller Hub (ICH) is used to manage data communications between a CPU and a motherboard. This specifically holds for Intel chipsets based on the Intel Hub Architecture. It is designed to be paired with a second support chip known as a northbridge. The ICH is used to connect and control peripheral devices. ICH2 …
Read More »The Biggest Examples of Machine Learning – Part 2
Smart machines and applications are steadily becoming a daily phenomenon, helping us make faster, more accurate decisions. The role of AI and machine learning is set to increase dramatically over the next five years, with more than 75 percent of businesses investing in Big Data. Organizations are spending almost 15 percent of their IT budget on machine learning capabilities. Let …
Read More »The Cost of Cyber Security Apathy
Evangelists give many costs to not taking security seriously – the risk of losing data, the risk of losing business reputation, and even the risk of being eliminated from the race altogether!! A recent survey puts the cost of a global cyber-attack as far reaching as $121.4 billion in an extreme event. This is roughly the same as losses caused …
Read More »Investment in Security vs. Loss in Cyber-attack?
In 2016, NATO took a landmark decision – not in terms of political insights, but in terms of recognizing the world for what it is today. With increasing proliferation of online data exchanges, social media and online enterprise operations, cyber security has become one of the biggest threats to modern business. Two years ago, NATO took cognizance of this fact and recognized …
Read More »The Biggest Examples of Machine Learning – Part 1
Smart machines and applications are steadily becoming a daily phenomenon, helping us make faster, more accurate decisions. The role of AI and machine learning is set to increase dramatically over the next five years, with more than 75 percent of businesses investing in Big Data. Organizations are spending almost 15 percent of their IT budget on machine learning capabilities. Let …
Read More »The Next Generation of Smart Fabrics
Almost every gadget you can think of is now going smart, Phones, watches, and even homes. I a bid to expand the technical horizons, researchers are looking for ways to make smart clothing. To do that, they need a smart fabric that can conduct electricity, but the textiles they’ve come up with thus far don’t breathe well and are rigid. …
Read More »
 Latest Technology News Today – Get Latest Information Technology Updates and Services Latest Technology News Today – Get Latest Information Technology Updates and Services
Latest Technology News Today – Get Latest Information Technology Updates and Services Latest Technology News Today – Get Latest Information Technology Updates and Services